The Resurgent Threat of Hacktivism
As the Russia-Ukraine conflict intensifies, cyberwarfare continues to be waged between the two countries. Concerns remain that state-backed hacker groups may target organisations outside of Eastern Europe in retaliation for the global sanctions imposed on Russia, or as false-flag operations to further promote political narratives. While the attention remains focused on nation-state cyberwarfare, another aspect organisations must also consider is the threat of non-state hacktivists. In an interview on CNBC’s ‘Mad Money,’ Crowdstrike CEO George Kurtz stated that, “e-crime actors are looking for a distraction and are ramping up their activities and stealing more money as the days go on .”
Indeed, the calls by cybersecurity leaders for a perspective shift, lead toward the dangers of militant hacktivist groups. The request by Ukrainian authorities for global volunteers to defend against the Russian ground invasion has also attracted hacker groups to secure the country’s cyber-frontlines. Since the opening days of the invasion, Ukrainian officials estimate 400,000 hackers have rallied to their aid through retaliatory strikes on Russian networks. According to Yuvall Wollman, president of cybersecurity firm CyberProof, “Grassroots volunteers created widespread disruption – graffitiing anti-war messages on Russian media outlets and leaking data from rival hacking operations.”
Cyberattacks on Russian Infrastructure

Russia has also been subject to cyberattacks on its own infrastructure since its incursion into Ukrainian territory on 24 February 2022. A day after the invasion’s commencement, the hacktivist collective known as ‘Anonymous,’ declared a cyberwar on Russia through its associated Twitter accounts. The decentralised hacker group, with a history of launching high-profile global cyberattacks, has often defaced government websites to promote narratives such as support for Taiwan’s sovereignty and to denounce web censorship policies.
On the 26th of February 2022, Anonymous’ Twitter accounts claimed responsibility for successfully attacking websites belonging to Russian media, state-owned companies, and government websites .
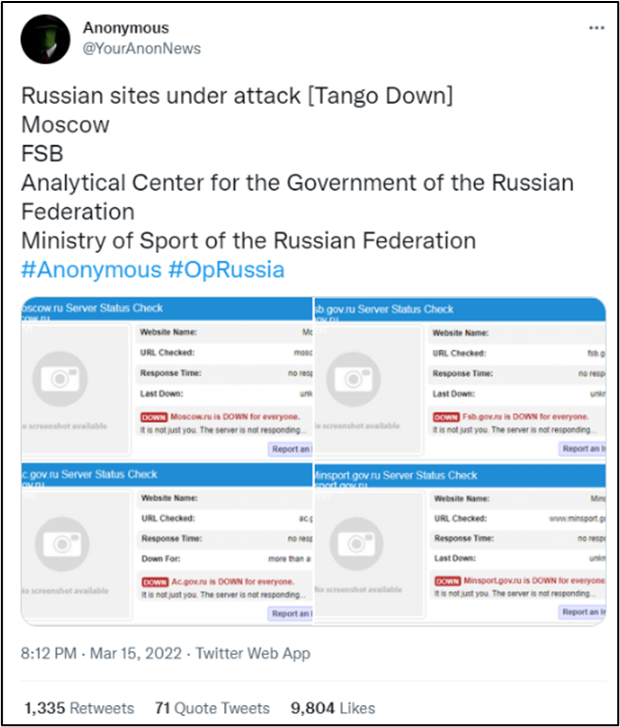
According to Russian Cyber Intelligence company Rostelecom-Solar, over 1,100 DDoS attacks on the Russian commercial sector were reported within the first ten days of March. The focus of these attacks has centred on Russian Government websites, where in one case, a portal received around 1,700 DDoS attacks within a span of 3 days. On the 15th of March, Anonymous announced that it had brought down four additional government websites that included a state-run think-tank called the Analytical Centre and the Federal Security Service (FSB ).
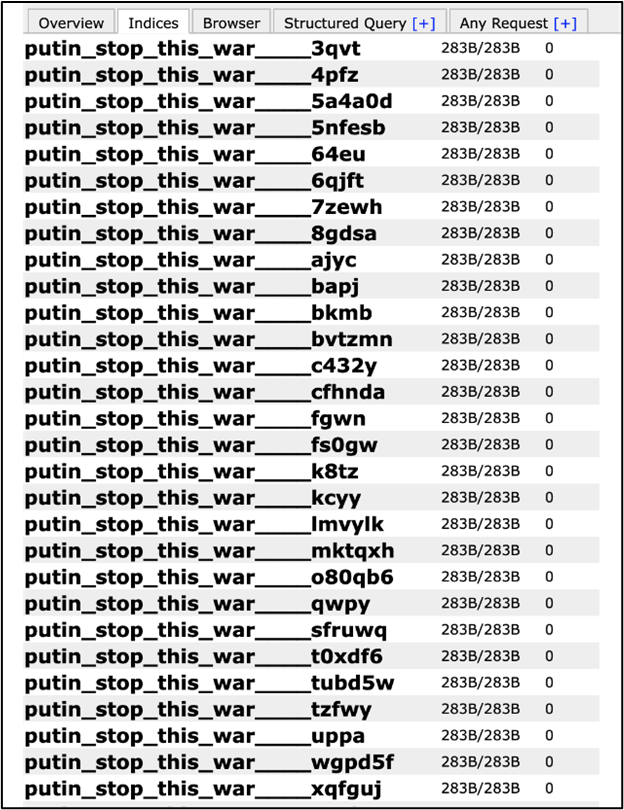
Cyberattacks have also compromised the databases of Russian retailers, internet providers and intergovernmental websites. Of a sample of 100 Russian databases, 92 were compromised according to Jeremiah Fowler, co-founder of the cybersecurity firm Security Discovery . These breaches were followed up by running malicious scripts to delete files and in some cases, rename them with political messages such as ‘putin_stop_this_war’. In addition, Fowler’s team had also determined that sensitive data such as employee names, email addresses, secret keys to encrypted data, and internal passwords were exposed. It is presently unknown what the original motive of the hack was , and whether the attackers had exfiltrated the sensitive data.
Russia’s Management of Their Cybersecurity Posture
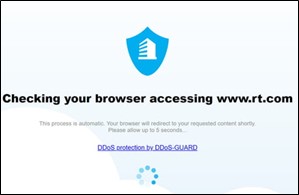
Initial coverage on Russia’s response to cyberattacks on its own IT infrastructure involve isolating government websites from international traffic . This method, known as ‘geofencing,’ can make Russian-based sites appear offline to international visitors, but are exclusively accessible within the country’s borders. Several Russian sites such as the state-controlled news network RT, continue to be accessible internationally, albeit with the addition of a browser checker to guard against further DDoS attacks. The actual effectiveness of Russian geofencing efforts remains in question however, as government sites have continued to fall victim to DDoS attacks and defacements by Anonymous and its counterparts . Follow-up claims of Russian site-outages by Anonymous on 15th March further suggest that the geofencing approach is inadequate as a long-term safeguard, and thereby warrants the need for additional security tools.
Western government sanctions have prohibited Certificate Authorities (CAs) from conducting business with Russia, preventing the renewal of TLS certificates that verify legitimacy and ensure secured data transmission to Russian websites . Consequently, modern web browsers will issue security warnings to deter or even block access to Russian sites with expired certificates. Russia has addressed this issue by creating its own CA to create certificates for domestic sites, although these are presently recognised exclusively by a Russian-based browser Yandex and Mail.ru’s Atom Browser . Users of common web browsers such as Google Chrome and Microsoft Edge may add the Russian certificate manually but raises security concerns that state-issued certificates may be exploited to conduct surveillance and cybercrime through HTTPS interception and Man-in-the-Middle attacks. Therefore, Russia’s initiative to counter the looming TLS certificate issue may achieve self-sufficiency at the price of additional cybersecurity threats to both domestic and international website visitors.
Russia has continued to reject involvement in using cyberattacks as a prelude to the invasion of Ukraine, instead placing blame on the United States for cyberattacks on its government systems and commercial bank websites . Despite having an alleged history of being responsible for launching cyberattacks on the U.S, NATO countries and its allies, the Kremlin appears to have adopted a non-escalatory stance in countering the recent rise in hacktivist attacks on Russian websites. One explanation is that Russian cyber-defence capabilities are heavily focused on offensive measures as compared to protective ones, which may explain the inability to stop the downing of prominent government websites despite the geofencing. However, this is unlikely, given that the country’s seasoned history of cyberwarfare. Another more feasible theory, is that the Kremlin is exercising restraint in displaying its cybersecurity capability to further assert its claim of non-involvement in the Ukrainian cyberattacks. This narrative is strengthened by the observation of Russia’s actions on 3rd March, when officials disclosed a list of over 17,500 unique IP addresses and 174 internet domains that allegedly performed DDoS attacks on domestic websites . Among these domains included the United States’ FBI and CIA homepages, as well as Ukrainian and several EU nations.
The Bottom Line: Prepare for Indiscriminate Cyberattacks
As the Russia-Ukraine conflict intensifies both on land and the internet, website owners must confront the reality that being caught in the crossfire is increasingly probable. While Russia faces growing isolation due to diplomatic sanctions and self-imposed geofencing, the prospect of launching retaliatory cyberattacks against targets worldwide may increase. Western governments have already warned its industries to prepare for Russian cyberattacks, although the example of Ukraine has raised concerns over whether the private sector can sustain prolonged assaults . As a result, the main factors organisations must consider are:
- Do not underestimate the threat of Hacktivism to your website: Global interconnectivity can rally thousands of hackers towards a common cause and impact the IT infrastructure of an entire country.
- Nation-states with renowned cybersecurity capabilities can still fall victim to cyberattacks: Organisations must incorporate restoration, and recovery methods along with preventative existing security measures.
- Defence-in-depth for website resilience is of paramount importance: Web administrators must review and perform risk assessment on the effectiveness of existing security tools to guard against DDoS and complex attacks.
- The risk of a global cybersecurity spill-over from the Russia-Ukraine cyberwar is real: While cyberwarfare is being waged to often further political agendas, hacktivist organisations may exploit these incidents to attack targets of opportunity for personal gain or other malicious purposes.
With the number of threat actors and attack vectors growing by the day, organisations are strongly advised to reinforce their security measures, be it in the form of implementing a web-application firewall, multi-factor authentication or regular antivirus scans. Protecting websites with a security tools stack can be a daunting task for organisations given the complexity of new capabilities by attackers. The WebOrion® Suite offered by Cloudsine addresses many of these challenges, providing a comprehensive security package that includes a fine-tuned Web-Application Firewall, Website Monitor and Restorer, enabling system operations teams to better prevent, detect and remediate cyberattacks.
If you are interested to learn more about how the WebOrion Suite can help you with your website’s protection, do contact us via our Contact Us Page.
For more information on how WebOrion can function as a countermeasure to web attacks and more, access our curated White Papers via the WebOrion Website.
Reference links:
- https://www.cnbc.com/2022/03/15/crowdstrike-ceo-cyber-crime-up-as-hackers-use-ukraine-war-as-distraction.html
- https://www.reuters.com/technology/russian-company-websites-hit-by-increased-hacking-march-says-cyber-firm-2022-03-11/
- https://www.geo.tv/latest/405548-russias-national-security-agency-hacked
- https://www.websiteplanet.com/blog/cyberwarfare-ukraine-anonymous/
- https://www.cnbc.com/2022/03/16/what-has-anonymous-done-to-russia-here-are-the-results-.html
- https://therecord.media/russia-appears-to-deploy-digital-defenses-after-ddos-attacks/
- https://www.datacenterdynamics.com/en/news/russian-government-websites-go-down-again-in-apparent-cyberattack/
- https://www.keyfactor.com/blog/russia-creates-its-own-certificate-authority-ca-to-issue-tls-certificates/
- https://www.bleepingcomputer.com/news/security/russia-creates-its-own-tls-certificate-authority-to-bypass-sanctions/
- https://thehill.com/policy/international/russia/595026-russia-denies-accusations-of-false-flag-operation-blame-for-cyber
- https://www.cyberscoop.com/russian-internet-ddos-incidents-ip-domain-list/
- https://www.theguardian.com/technology/2022/mar/10/us-russia-cyber-attack-prepared
Authored by Toby Lim, Associate Security Consultant
Edited By Cloudsine – WebOrion Security Team


